Deepfakes now span voice, video, and digital identity impersonations. Whether used in phishing, vishing, smishing, social engineering, or CEO fraud, these threats bypass traditional security controls. Worse yet, traditional detection tools today aren’t made to detect AI-generated threats or require coding to operationalize.

Traditional cybersecurity focuses on OSI Layers 1 through 7. Agentic AI targets the human, which requires a new approach. We call this Layer 8, the Human Layer.
Your people are the #1 attack vector. Netarx stops impersonation threats before trust is exploited—protecting your employees, executives, customer interactions, and the integrity of your brand. Most organizations have no protection from social engineering. AI-generated threats target your employees simultaneously across voice, email, messaging, and video.
Ingest data from your live communications and applications
Use proprietary and federated AI models for signal analysis
Cross-reference identities with encrypted validators such as metadata or custom attributes for your organization
Detect anomalies and alert in real time
Enables users to stop synthetic threats before damage is done
Gain shared awareness to cross-check identity signals across multiple channels — metadata, behavioral patterns, communication history, and context.
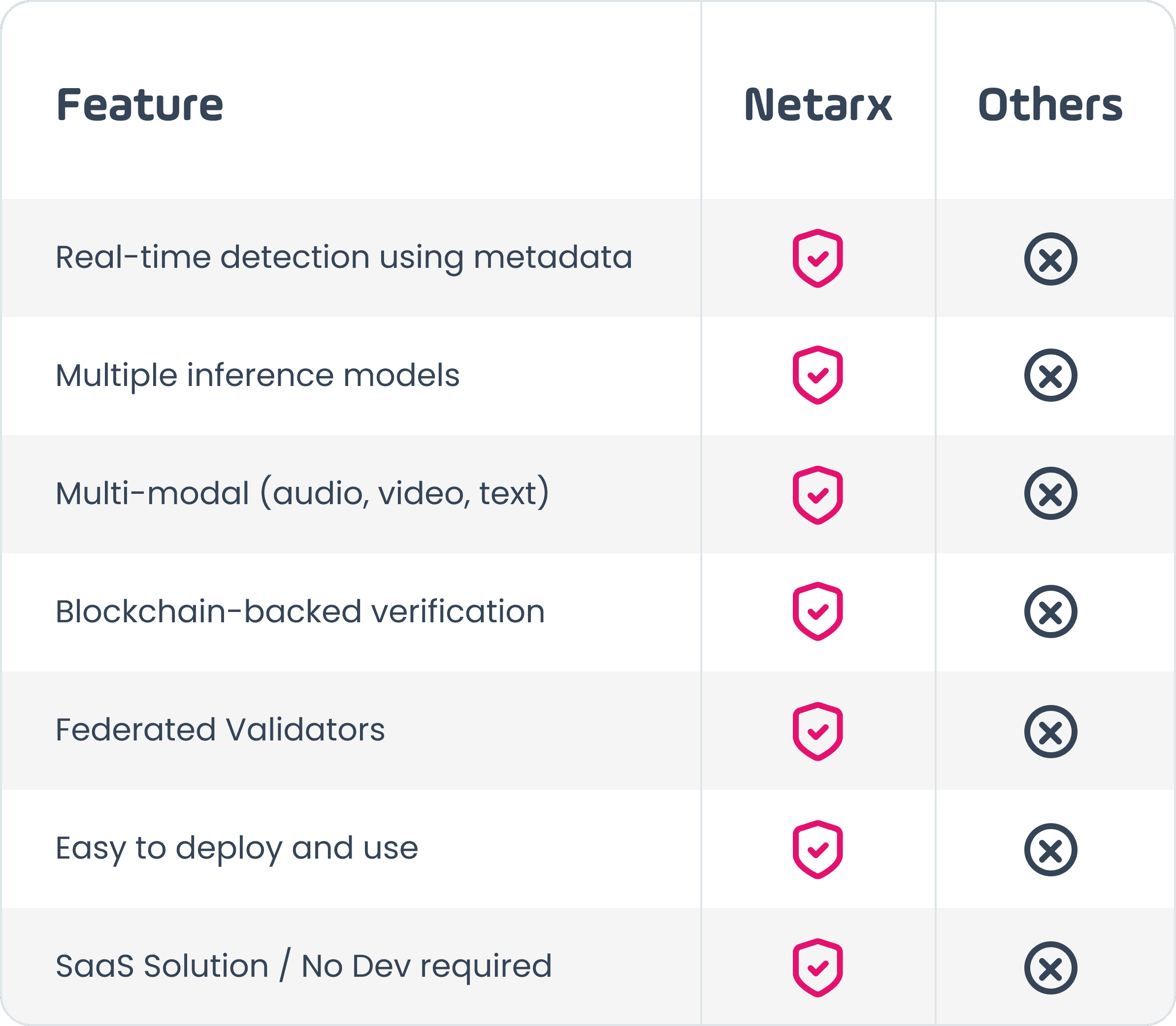
Netarx is the only cybersecurity platform purpose-built to detect impersonations from deepfake attacks across all media in real time—across video, audio, texts, and synthetic identity threats.
Netarx sets itself apart from other solutions by combining advanced media detection with robust identity validation, creating a comprehensive defense against modern threats. While other solutions focus solely on detecting synthetic media, Netarx goes a step further by also verifying the authenticity of the individual behind the interaction. This can be accomplished because netarx aggregates metadata across the communications channels (email, meetings, texts, phone, etc).
Our platform starts with leveraging media detection to identify deepfakes and other synthetic content, ensuring that malicious attempts are flagged before they can cause harm. Simultaneously, we validate the individual’s identity through cryptographic and device-level assurance, making impersonation and social engineering attacks significantly more difficult to execute.
This dual-layered approach ensures not only the integrity of the media but also the authenticity of the person, delivering a level of accuracy that single-focus solutions simply cannot match. In an advanced enterprise security stack, AI-based deepfake detection is the first line of defense against external impersonation attempts.
Existing security tools, like Identity Threat Detection and Response (ITDR) and Identity Validation (IDV), provide visibility into internal misuse of identity and access if credentials are breached or manipulated. Netarx supplements traditional cybersecurity to protect against fraud BEFORE an organization is breached. Security paradigms like Zero Trust are out-dated. With Netarx, you don’t need rely on trust…identity is verified. In a world of synthetic threats, Netarx replaces trust with proof. No Trust Needed.
Other deepfake detection and protection solutions suffer from one or more critical gaps:
They only look for synthetic media. They don't authenticate the user.
They suffer from accuracy issues (due to limited context, data, and shared awareness).
They require integration or coding to tie into your stack.
They are limited to one or maybe two inference models.
They support only one media like video-only requiring organizations to bring in multiple vendors.
They are difficult to use...especially by the end-user.
They are prone to hacking by quantum-based computing
They can’t support federated validators - independent verification nodes that collectively validate information, identity, and transactions.
netarx is designed to comprehensively detect and protect your organization from impersonations across video, email, and voice communications. Don't just detect AI-generated media. Protect from impersonations.